Executive Summary
The modern finance function, once built on ledgers and guarded by policy, now lives almost entirely in code. Spreadsheets have become databases, vaults have become clouds, and the most sensitive truths of a corporation including earnings, projections, controls, and compensation exist less in file cabinets and more in digital atmospheres. Throughout my twenty-five years leading finance across cybersecurity, SaaS, manufacturing, logistics, and gaming, I have learned that with this transformation has come both immense power and a new kind of vulnerability. Finance, once secure in the idea that security was someone else’s concern, now finds itself at the frontlines of cyber risk. When cyber risk is real, it is financial risk. And when controls are breached, the numbers are not the only thing that shatter. So does institutional confidence.
From Cybersecurity to Financial Resilience
The vocabulary of cybersecurity has long been technical, coded in the language of firewalls, encryption, threat surfaces, and zero-day exploits. But finance speaks a different dialect: exposure, continuity, auditability, and control. The true challenge is not simply to secure the digital perimeter. It is to translate cybersecurity into terms of governance, capital stewardship, and business continuity.
At the core of this transformation lies data governance, a term that feels bureaucratic but is in fact existential. The finance function is uniquely data-intensive. Forecasting, compliance, scenario modeling, and shareholder reporting all rely on the integrity of structured data. Yet in many organizations, data governance is fragmented. Spreadsheets circulate beyond their owners. Sensitive assumptions are stored in personal folders. Access rights sprawl.
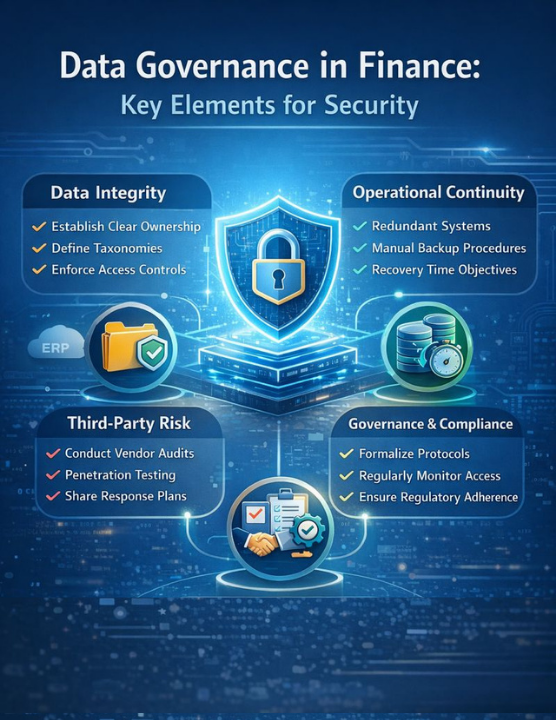
Finance Cyber Risk Framework
| Risk Dimension | Vulnerability | Governance Control | Resilience Measure |
| Data Integrity | Uncontrolled spreadsheets, fragmented ownership | Data taxonomies, master records, role-based access | Version control, audit trails, encryption at rest/transit |
| Operational Continuity | Single points of failure, locked systems | Redundant systems, degraded mode design | Recovery time objective, manual fallback procedures |
| Third-Party Exposure | Vendor attacks, API vulnerabilities | Vendor security audits, penetration tests | Shared incident response plans, contract terms |
| Access Management | Privilege creep, orphaned accounts | Role-based provisioning, quarterly reviews | Automated de-provisioning, multi-factor authentication |
| Recovery Capability | No tested backup, unclear restoration | Documented recovery procedures, regular tests | Recovery point objective, restoration time tracking |
| Regulatory Compliance | Incident reporting gaps, disclosure delays | Formalized incident protocols, legal coordination | Board notification procedures, regulatory filing readiness |
Good governance begins with clarity: what data exists, who owns it, who touches it, and where it flows. Finance must work hand-in-glove with IT to establish data taxonomies, define master records, enforce role-based access, and ensure encryption in transit and at rest. This is not busywork. It is the scaffolding of cyber hygiene.
When I led finance at a cybersecurity firm, we implemented comprehensive data governance protocols for financial systems. We classified all financial data by sensitivity level, established role-based access with quarterly reviews, and enforced encryption for all data at rest and in transit. We conducted quarterly disaster recovery tests simulating ransomware scenarios affecting our ERP system. These tests revealed that our initial recovery time objective of 24 hours was inadequate for payroll processing. We redesigned our backup architecture, established manual payroll processing procedures, and achieved a 4-hour recovery capability for critical financial processes.
Designing for Resilience
But governance is only the beginning. The real test lies in continuity. Cyber risk does not always appear as a breach. Sometimes it appears as latency. A payroll file that fails to transmit. A trading system that goes dark. A treasury platform locked by ransomware.
Critical Resilience Questions:
- What happens if our accounts payable system is locked for 48 hours?
- What if our cloud provider is compromised?
- What if our vendors become attack vectors?
- Which processes must remain manual-capable should automation fail?
Resilience means designing finance systems with degraded modes, ensuring that key processes like payroll, fund transfer, and regulatory filing can continue even if other systems are compromised.
Third-Party Risk and CFO Leadership
Cyber risk also brings a strategic lens to third-party exposure. In an increasingly connected ecosystem including outsourced payroll, cloud ERPs, digital banks, and fintech APIs, finance’s risk perimeter is now shared with others. Vendor due diligence, once a procurement checkbox, must now include cybersecurity audits, penetration tests, and shared incident response plans.
As this landscape evolves, the CFO must take a more active seat at the cybersecurity table. Cybersecurity is not solely an IT concern. It is a financial one. It affects liquidity planning, insurance coverage, regulatory exposure, and reputational capital. It demands board-level attention and enterprise-level investment.
The future of managing cyber risk in finance lies in integration. Not in building walls but in building bridges between IT and financial planning and analysis, between security protocols and business rules, between resilience architecture and capital planning. Finance professionals do not need to become technologists. But they must become interpreters, able to translate digital risk into economic consequence and to shape investment decisions accordingly.
Strategic Investment in Resilience
To lead effectively, CFOs must go beyond cost-benefit analyses of security tools. They must think in terms of systemic resilience:
- What are the controls that matter most?
- What is our recovery time objective?
- What are the systems of record we cannot afford to lose?
- Which processes must remain manual-capable should automation fail?
These are financial design questions. And they demand financial stewardship.
My certifications as a CPA, CMA, and CIA emphasize internal controls, risk management, and governance frameworks. But what separates finance organizations that withstand cyber incidents from those that fracture is not security tool investment alone. It is the governance discipline to classify and control data systematically, the resilience architecture to operate under degraded conditions, and the strategic leadership to translate cyber risk into economic terms that drive appropriate enterprise investment in continuity and recovery capabilities.
Conclusion
Resilience is not a project. It is a philosophy. And in a world where the invisible breach can shape the visible outcome, it may be the most important capital a CFO can build. Managing cybersecurity risk in finance is not about responding to the last attack. It is about preparing for the next one and the one after that. It is about designing systems that are not only efficient in normal times but defensible in moments of failure.
Disclaimer: This blog is intended for informational purposes only and does not constitute legal, tax, or accounting advice. You should consult your own tax advisor or counsel for advice tailored to your specific situation.
Hindol Datta is a seasoned finance executive with over 25 years of leadership experience across SaaS, cybersecurity, logistics, and digital marketing industries. He has served as CFO and VP of Finance in both public and private companies, leading $120M+ in fundraising and $150M+ in M&A transactions while driving predictive analytics and ERP transformations. Known for blending strategic foresight with operational discipline, he builds high-performing global finance organizations that enable scalable growth and data-driven decision-making.
AI-assisted insights, supplemented by 25 years of finance leadership experience.










