Executive Summary
In the past decade, “Zero Trust” has become the cybersecurity mantra of modern enterprise strategy: oft-invoked, rarely clarified, and even more rarely implemented with conviction. It promises a future where no user, device, or workload is trusted by default. It assures boards and regulators of reduced breach risk, minimized lateral movement, and improved governance in a hybrid, perimeterless world. But for most Chief Information Officers, the question is not “Why Zero Trust?” but how to implement it. Where to start. What to prioritize. How to measure progress. And perhaps most critically, how to embed it into existing business systems without disrupting continuity or creating resistance from teams already under pressure. This framework provides a strategic approach for CIOs seeking to operationalize Zero Trust not as a buzzword or compliance checklist but as an enterprise security architecture with tangible outcomes.
Zero Trust: The Core Principle
At its heart, Zero Trust is a security model built on the assumption that no user, device, or process should be inherently trusted. Access is granted only after strict verification and is continuously reassessed based on context, behavior, and risk posture.
Throughout thirty years leading finance and operations across cybersecurity, SaaS, gaming, logistics, and manufacturing organizations, I have witnessed how implementing Zero Trust requires undoing decades of implicit trust architectures.
Zero Trust is not a single product but an operating model that spans five architectural domains:
- Identity (who are you?)
- Device (what are you using?)
- Network (where are you coming from?)
- Application and Workload (what are you accessing?)
- Data (what are you doing with it?)
Implementing Zero Trust means building controls and telemetry across all five, aligned to least privilege, continuous verification, and assumed breach principles.
The Phased Implementation Roadmap
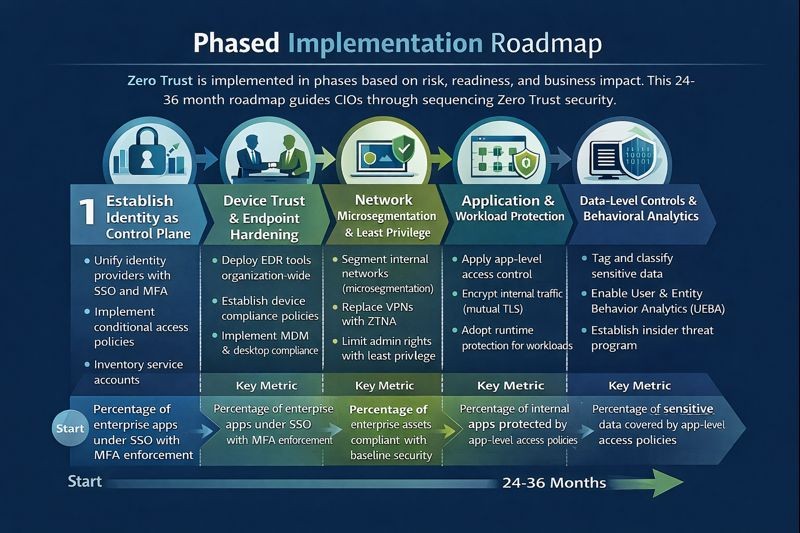
Zero Trust Implementation Framework
The following framework maps the phased approach to measurable outcomes:
| Implementation Phase | Timeline | Key Activities | Success Metrics | Business Impact |
| Phase 1: Identity | Months 1-6 | Unify IdPs, deploy SSO/MFA, inventory service accounts | 90%+ apps under SSO/MFA | Reduced credential theft, simplified access |
| Phase 2: Device | Months 6-12 | Deploy EDR, establish compliance policies, implement MDM | 95%+ endpoints compliant | Prevented compromised device access |
| Phase 3: Network | Months 12-18 | Microsegmentation, ZTNA deployment, least privilege | 50%+ reduction in lateral paths | Limited breach impact radius |
| Phase 4: Application | Months 18-24 | App-level access control, mutual TLS, runtime protection | 80%+ apps with access policies | Protected sensitive applications |
| Phase 5: Data | Months 24-36 | Data classification, UEBA, insider threat programs | 90%+ sensitive data classified | Prevented data exfiltration |
Enablers of Success
Executive Sponsorship and Change Management
Zero Trust must be a strategic imperative owned by senior leadership, including the CIO, CISO, and business leaders. Align Zero Trust implementation with enterprise risk appetite. Communicate security as enabler, not barrier.
Vendor Consolidation and Architecture Simplification
CIOs must resist stacking tools without architectural coherence. A fragmented Zero Trust ecosystem leads to visibility gaps and friction.
Best practices:
- Favor platforms with integration and automation capabilities
- Build around a unified identity fabric and common policy engine
- Rationalize legacy infrastructure that contradicts Zero Trust principles
Continuous Monitoring and Automation
Zero Trust is not static. Threats evolve. Implement real-time monitoring for drift in posture. Automate remediation and access revocation where feasible. Adopt a trust-but-verify loop, powered by telemetry and behavioral analytics.
Zero Trust Maturity Model
CIOs should adopt a maturity model to assess and communicate progress to stakeholders:
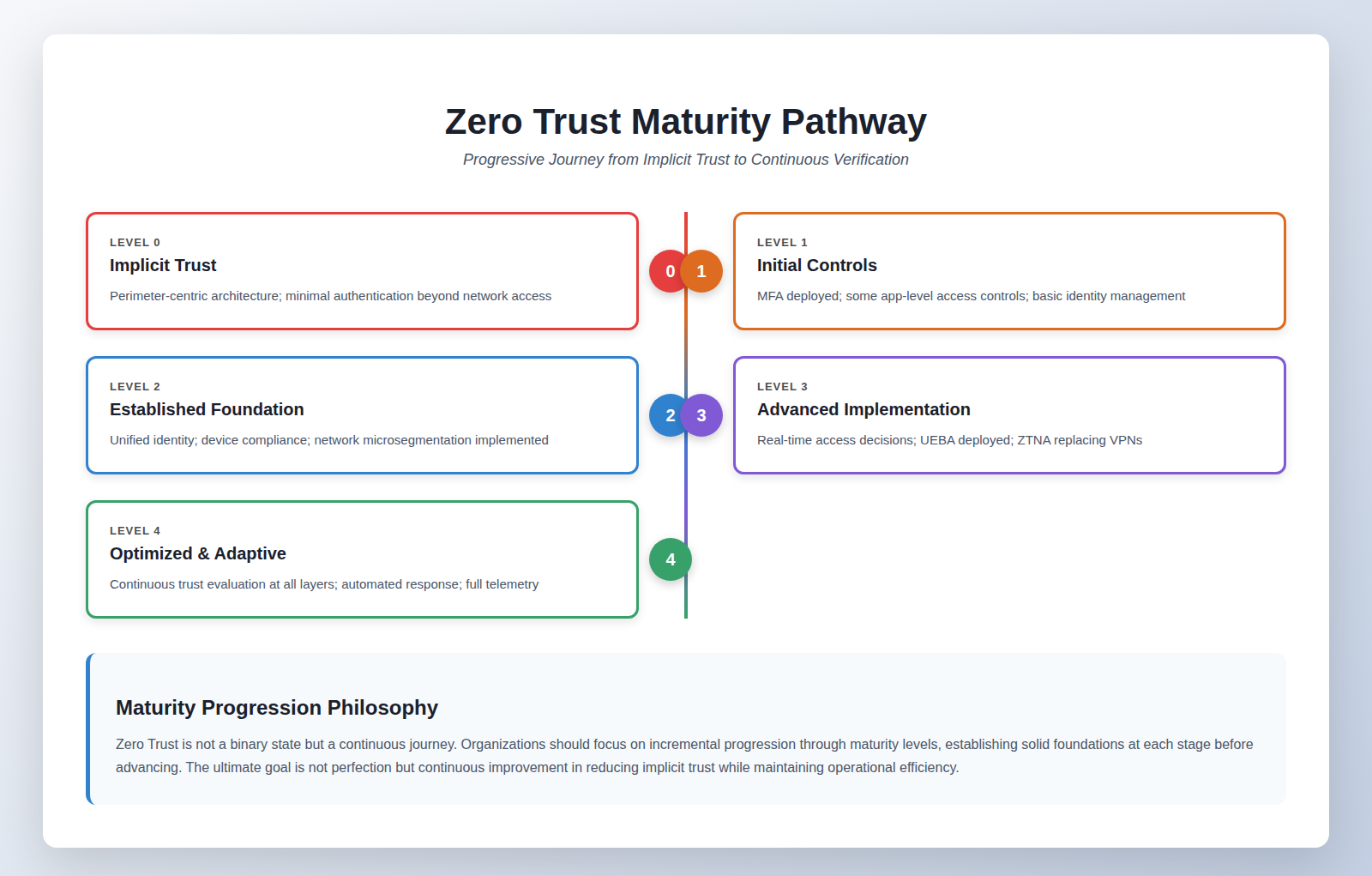
The goal is not perfection but continuous improvement and risk alignment.
Conclusion
Zero Trust is not merely a cybersecurity project but a reorientation of enterprise architecture around verification, visibility, and least privilege. For CIOs, the mission is to move from theory to action, step by step, domain by domain, guided by metrics and anchored in business value. In an age where perimeters no longer exist, where threats originate from within as much as without, and where data and workloads move across clouds and devices in milliseconds, Zero Trust is not optional but essential. The implementation journey is complex, but the payoff in resilience, agility, and confidence is worth every phase.
Disclaimer: This blog is intended for informational purposes only and does not constitute legal, tax, or accounting advice. You should consult your own tax advisor or counsel for advice tailored to your specific situation.
Hindol Datta is a seasoned finance executive with over 25 years of leadership experience across SaaS, cybersecurity, logistics, and digital marketing industries. He has served as CFO and VP of Finance in both public and private companies, leading $120M+ in fundraising and $150M+ in M&A transactions while driving predictive analytics and ERP transformations. Known for blending strategic foresight with operational discipline, he builds high-performing global finance organizations that enable scalable growth and data-driven decision-making.
AI-assisted insights, supplemented by 25 years of finance leadership experience.